- HOME
- Products & Services
- IT service
- Breach Risk Minimization
Products & Services
Breach Risk Minimization
With the rapid growth of IoT and BYOD, the number of IT assets managed by companies continues to increase, and the attack methods for these diverse systems are becoming more complex. Balbix uses specialized AI algorithms to discover and analyze the enterprise attack surface to give a 100x more accurate view of breach risk.
Overview
Balbix uses specialized AI algorithms to discover and analyze the enterprise attack surface to give a 100x more accurate view of breach risk.
Balbix also provides a prioritized set of actions that you can take to transform your cybersecurity posture and reduce cyber-risk by 95% or more, while making your security team 10x more efficient.

Feature
・Sensors, connectors, and collectors deployed across your network continuously discover and monitor your devices, apps, and users across 100+ attack vectors.
・The Balbix Brain uses specialized AI to predict likely breach scenarios and prescribes a prioritized set of necessary actions to improve cybersecurity posture.
・Integrations with ticketing and orchestration systems enable you to operationalize the transformation and maintenance of your cybersecurity posture.
Use Case
Balbix BreachControl also provides a prioritized set of actions that you can take to transform your cybersecurity posture and reduce cyber-risk by 95% or more, while making your security team 10x more efficient.
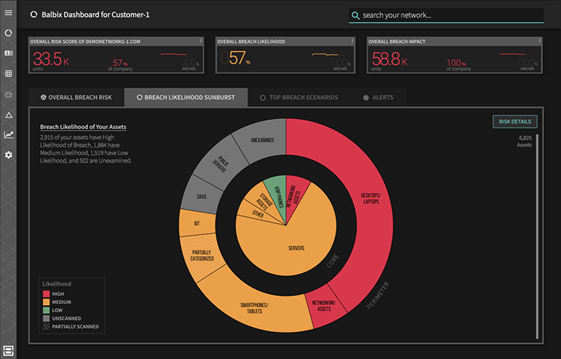
Automatic Asset inventory
With Balbix you do not need to specify what to scan as Balbix automatically (and continuously) discovers and categorizes your assets, i.e., any devices, applications and users present on your extended network, and analyzes them for vulnerabilities. Balbix also estimates business criticality for each asset based on analysis of usage and network traffic.

Real time and continuous, with natural language searchBalbix is real-time and operates continuously and automatically. The risk model surfaced by Balbix is usually seconds or less behind the actual on-network conditions, and you can answer questions about your cybersecurity posture and risk using google-like natural language search.

IoT and OT
Balbix discovers, categorizes, and analyzes IoT and OT assets in your network for cyber-risk. Balbix also prescribes mitigations for these assets differently– focusing more on practical compensating controls than on patching.

Cloud SecurityBalbix is able to discover, observe and analyze all of your cloud assets, including resources available only via API. For each asset, Balbix will provide you with insights into how the asset is being used and by whom, plus an assessment of cybersecurity configuration and whether it presents cyber-risk to the organization.
Related products
Documents
Data Sheet
Contact Us
Please feel free to contact us.




 Contact Us
Contact Us
 Download documents
Download documents
 Member services
Member services